This table lists common hash encryption formats, how to identify them, and the corresponding John the Ripper command for cracking them.
| Encryption Type | Hash Start | Example Hash | How to Identify | John the Ripper Command |
|---|---|---|---|---|
| DES | 2 chars (salt) | Ep1t0mE9h68JI |
13 chars, starts with 2-char salt (a-z, A-Z, 0-9, ./) | john --format=des file.txt |
| MD5 | $1$ |
$1$Ep1234$abcde12345fghij67890 |
Starts with $1$, salt (up to 8 chars), hash | john --format=md5crypt file.txt |
| SHA-256 | $5$ |
$5$Ep12345678$abcde12345fghij67890abcdef1234567890 |
Starts with $5$, salt, long hash | john --format=sha256crypt file.txt |
| SHA-512 | $6$ |
$6$Ep12345678$abcde12345fghij67890abcdef1234567890abcdef1234567890abcd |
Starts with $6$, salt, very long hash | john --format=sha512crypt file.txt |
| Blowfish (bcrypt) | $2a$ or $2y$ |
$2a$12$Ep1234567890$abcde12345fghij67890ab |
Starts with $2a$ or $2y$, cost (e.g., 12) | john --format=bcrypt file.txt |
Example DES:
Step 1: Generating a DES-Encrypted Password Hash
perl -e 'print crypt("123456", "Ep") . "\n";'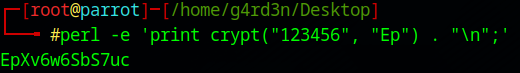
Step 2: Storing the Hash in a File
echo "test_user:EpXv6w6SbS7uc" > hash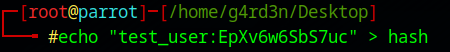
Step 3: Cracking the Hash with John
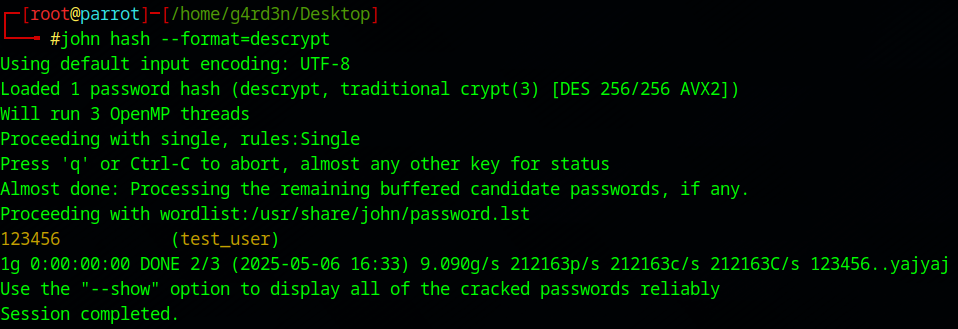
john hash --format=descrypt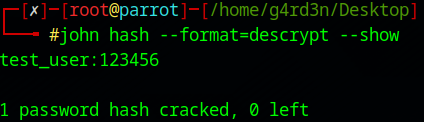
john hash --format=descrypt --show